28. Reports » Tools » Firewall¶
Reports » Tools displays the number of firewall rules that have new matches in the last 5 seconds.
The Firewall tab lists all firewall rules managed by Wanguard and provides a quick and easy way for Console users to define their own rules. The tab contains 3 sub-tabs, located at the lower left side of the window:
28.1. Active Firewall Rules¶
It displays the active rules generated automatically by Filters or introduced manually by Console users.
Administrators and operators can add and delete firewall rules manually. To add a new rule, click the [Create Firewall Rule] button and then choose one of the existing firewall options from the drop-down menu. The firewalls that are not defined in Filter configurations are hidden. [Reset] deletes all firewall rules from the database without actually updating the firewall.
The Create Netfilter Firewall Rule window provides the following options:
● Description – A short name that helps you identify the firewall rule. This is the only mandatory field● Filter(s) – Select the Filter that will apply your rule (considering their configuration: interfaces, Netfilter Chain, Netfilter Table, etc.)● Direction – Select Inbound to match packets entering your network (through interfaces defined as Inbound in the Filter Configuration window). Otherwise, select Outbound● IP Protocol(s) – Select one or more IP protocols, or Any to match all packets● Source/Destination IP/mask – Enter to match packets by their source or destination IP blocks. The mask is optional and values without it are considered hosts (mask defaults to /32 for IPv4 and /128 for IPv6)● Source/Destintation Port(s) – This field is editable only for the following IP protocols: TCP, UDP, UDPLITE, DCCP, and SCTP. It matches a set of source or destination ports. Up to 15 ports can be specified (e.g. 53, 1024:65535 would match ports 53 and all from 1024 through 65535)● IP Packet Length – It is used to match the length of the layer-3 payload (e.g. layer-4 packet) against a specific value or range of values separated by “:”● IP TimeToLive – It is used to match the TTL field from the IP header. If the value is preceded by “>”, then the packet is matched if TTL is greater than the given TTL value. If the value is preceded by “<”, then the packet is matched if TTL is less than the given TTL value● TCP Flags Set/Unset – Select the TCP flags that must be explicitly set and/or unset. TCP flags that are not enabled in either fields are ignored● Payload Content – Enter to match a string anywhere in the packet. Use this option with caution as it consumes a lot of CPU resources● Country(ies) – Select to match packets by their country of origin. This option can be used only after installing the xp_geoip Netfilter module● Firewall Policy – Select the Netfilter Firewall policy applied for the matched packets:◦ Drop – blocks the packets◦ Reject – blocks packets and sends an ICMP reply packet indicating the port is unavailable◦ Accept – allows packets to pass the firewall◦ Rate Limit – allows a limited number of packets through the firewall● Rate Limit – You can use this parameter to limit rate of packets per time unit to a predefined value. If the value ends with the character “b” then the rate-limiting is applied for bytes not packets● Rate Limit Hashing – You can apply the rate-limiting globally, to a single object (Src. IP, Src. Port, Dst. IP or Dst. Port) or to any combination of objects. If the rate-limiting should be connection-oriented, select all objects. To rate-limit the packet or byte rate of each source IP, select the Src. IP object● Rule Active Until – Select Manually deleted to apply the firewall rule indefinitely. Select the other options to remove the firewall rule after a predefined condition
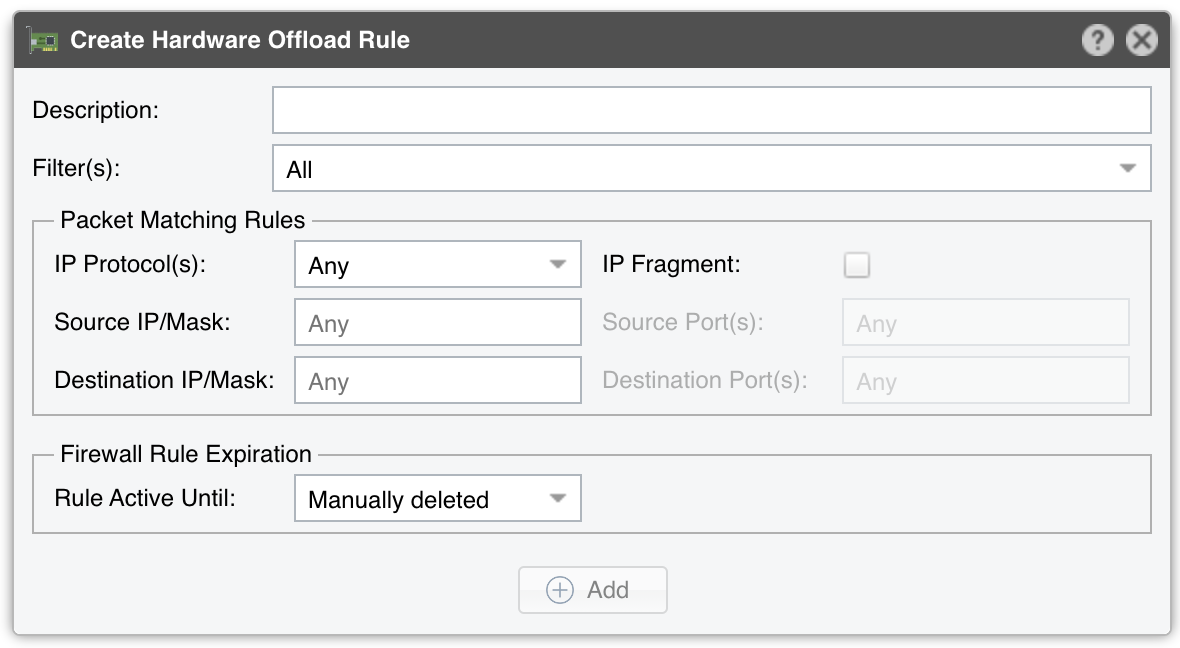
The Create Hardware Offloading Rule window contains the following options:
● Description – A short name that helps you identify the rule. This is the only mandatory field● Filter(s) – Select the Filter that will apply your rule● IP Protocol(s) – Select one or more IP protocols, or Any to match all packets● IP Fragment – Select to match only fragmented packets● Source/Destination IP/mask – Enter to match packets by their source or destination IP blocks. The mask is optional and values without it are considered hosts (mask defaults to /32 for IPv4 and /128 for IPv6)● Source/Destination Port(s) – This field is available only for the following IP protocols: TCP, UDP, UDPLITE, DCCP and SCTP. It matches a set of source or destination ports. Up to 15 ports can be specified (e.g. 53, 1024:65535 would match ports 53 and all from 1024 through 65535)● Rule Active Until – Select Manually deleted to apply the firewall rule indefinitely. Select the other options to remove the firewall rule after a predefined condition
The Create Dataplane Firewall Rule window contains fields that are already explained by the previous paragraph.
When there is at least one active firewall rule, a table describing it and showing the exact number of matches is displayed in the content area.
28.2. Filtering Rule Archive¶
Lists filtering rules detected by the selected Filter(s) for the selected time range. Most fields are described in the “Reports » Tools » Anomalies” chapter.