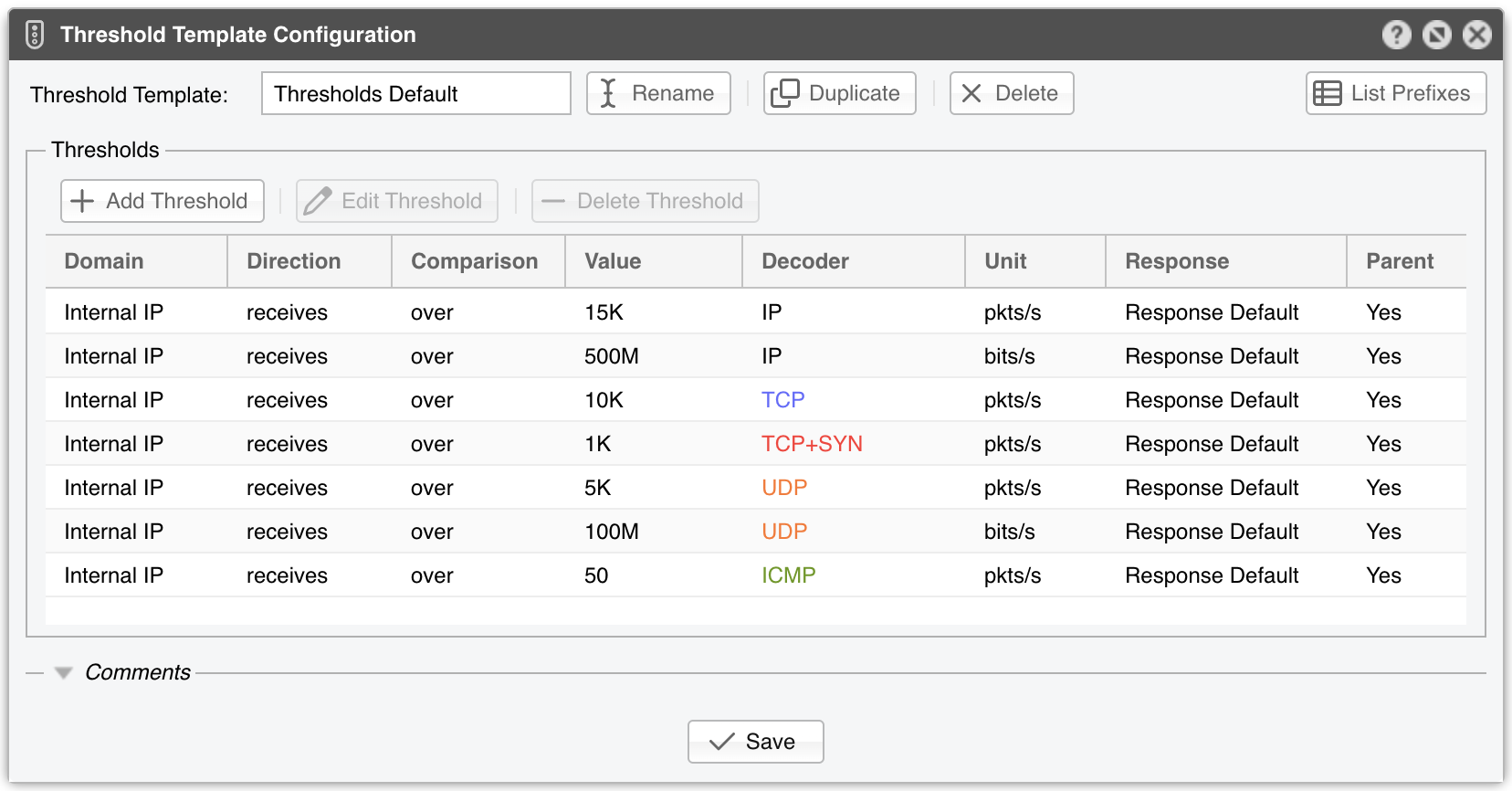
14. Network & Policy » Threshold Template¶
Every threshold rule contains the following metrics:
● Domain – Sensors can detect anomalies to/from an internal IP contained in the selected subnet or to/from the subnet taken as a whole. If the selected subnet is 0.0.0.0/0, then a third option is possible, which allows detection anomalies to/from external IPs (for this third option to work, the Stats Engine parameter from the Sensor configuration has to be set accordingly)● Direction – The direction of traffic can be receives for the inbound traffic received by the prefix or sends for the outbound traffic sent by the prefix● Comparison – Select over to detect volumetric anomalies (e.g., DrDoS, DDoS), or under to detect a gap in the expected traffic● Value – The threshold value can be entered as an absolute number or as a percentage of the total traffic matched by the selected decoder per Sensor interface. Absolute values can be multiples of 1000 with K (kilo) appended, multiples of 1 million with M (mega) appended, or multiples of 1 billion with G (giga) appended● Decoder – Select one of the decoders enabled in General Settings » Anomaly Detection● Unit – DDoS attacks usually reach a very high number of packets per second, so the pkts/s option is the best way to detect them. For bandwidth-related anomalies, select bits/s● Response – Select a previously defined Response, or select None to have no reaction to anomalies other than displaying them in Reports » Tools » Anomalies » Active Anomalies● Parent – Select Yes if more specific prefixes should inherit the threshold. You can cancel inherited thresholds by defining a similar threshold with Unlimited selected in the Value field● Inheritance – Displays the parent prefix when the rule is inherited from a less specific prefix
Note
Adding similar threshold rules in the same prefix or Threshold Template is not allowed, even when the rules have different values or Responses. To execute different actions for different threshold values, define only the smallest threshold value, and then make use of preconditions inside the Response. For example, if you want to activate Wanguard Filter for UDP attacks stronger than 100 Mbps but you also want to null-route them when they reach 1 Gbps, add only the “Internal IP receives over 100M UDP bits/s” rule. Then, inside the Response add two actions: one that activates Filter without preconditions, and another that executes the null-routing BGP announcement with the precondition “Peak Value” “greater than” “1G”.