10. General Settings » Anomaly Detection
The anomaly detection engine can be configured in Configuration » General Settings » Anomaly Detection. The detection of anomalies also needs to be enabled individually for each subnet defined in the IP Zone.
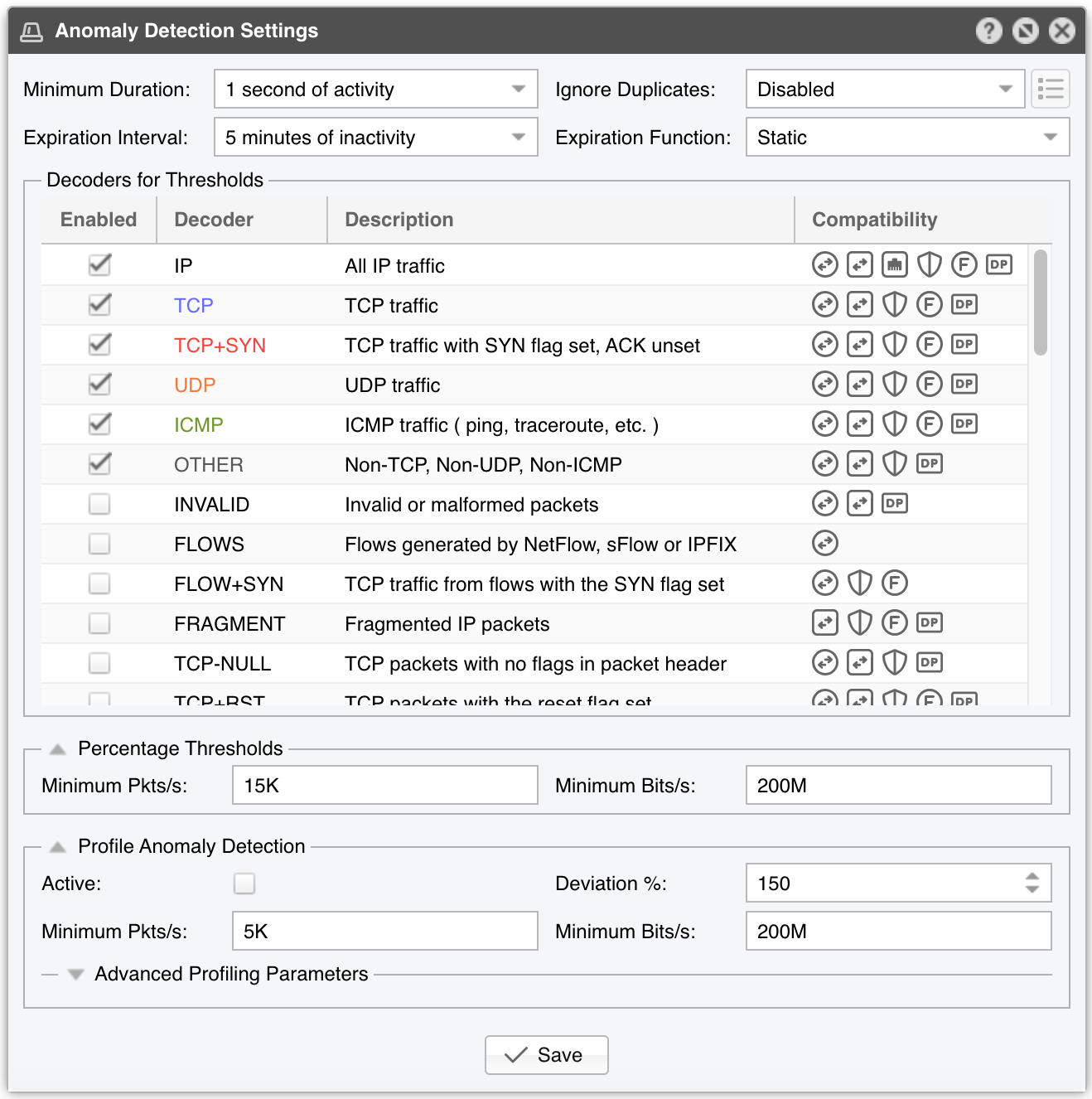
● Minimum Duration - Can be used to avoid reporting anomalies that are shorter than a predefined number of seconds. When using Flow Sensor, the flow delay must be taken into consideration. If the first option is selected, the anomalies will be reported without delay because 1 second is the shortest time frame used to calculate traffic rates
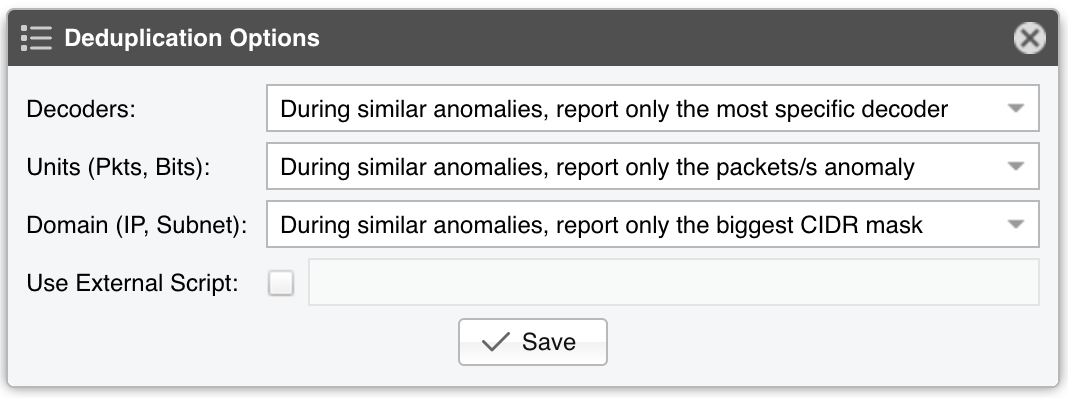
● Ignore Duplicates - Enable if you want to prevent the reporting of multiple anomalies for the same attack. Similar anomalies are the anomalies that share the same start time. When this option is enabled, click on the options button from the right-hand side, and select which anomalies should be ignored:
• Decoders - When this option is not used, if you define a 500k pps threshold for the IP decoder, a 400k pps threshold for the TCP decoder, and a 30k pps threshold for the TCP+SYN decoder, and then a 600k pps TCP+SYN attack is being received, the Sensor will detect three anomalies, one for each decoder. With this option, the Sensor will report a single anomaly for the most specific decoder, which in this case is TCP+SYN
• Unit (Pkts,Bits) - Use this option to ignore the anomaly for a bits/s threshold when a similar anomaly exists for a packets/s threshold
• Domain (IP,Subnet) - Use this option to ignore the anomalies detected by parent prefix(es) when a similar anomaly is detected for a more specific prefix (e.g. if you define a threshold for a /24 and a similar anomaly is detected towards a /32 included in the /24 subnet, only the /32 anomaly will be reported). If the threshold value of the less specific prefix is higher, and a more specific prefix is being reported, the traffic value of the more specific prefix is subtracted from the less specific prefix when comparing it to the threshold
•
Use External Script - You can decide whether an anomaly will be reported or not by using a custom script that accepts
dynamic parameters as arguments. If the exit status of the script is non-zero, the anomaly will not be reported. The usage is similar with the technique described in the
Response chapter
● Expiration Interval lets you select the number of minutes of inactivity before anomalies expire. The default value is 5 minutes. When using Flow Sensor, the flow delay must be taken into consideration, so don’t lower the default value unless you really know what you’re doing
● Expiration Function can be used to increase (linearly or exponentially, both for up to 24 hours) the number of minutes of inactivity before recurring anomalies expire. The system takes into account similar anomalies received in the previous seven days
Wanguard Sensor detects traffic anomalies using two different methods:
10.1. Threshold Anomalies
Threshold Anomalies are breaches of user-defined traffic thresholds. These thresholds can be defined inside IP Zones for the decoders enabled in the Decoders for Thresholds list. Decoders represent internal functions (traffic dissectors) that differentiate and classify the underlying protocols of each packet or flow.
Enable only the decoders for which you need to define thresholds. The Compatibility column shows you if Packet Sensor, Flow Sensor or SNMP Sensor can use the decoder to detect anomalies, and if these anomalies could be mitigated by Packet Filter with Netfilter, or using Flowspec or the Dataplane Firewall.
Thresholds can include either absolute values (e.g. IP receives 100k UDP packets/s) or percentage values (e.g. IP receives 30% UDP packets/s). To prevent Percentage Thresholds from being triggered for small amounts of traffic, configure minimum packets/s and bits/s values. Percentage values are calculated based on the rates of the monitored interface, for the same decoder. E.g., for an interface that receives 100k UDP packets/s, a 30% UDP packets/s threshold defined for a single IP triggers an anomaly when the IP receives over 30k UDP packets/s.
10.2. Profile Anomalies
Profile Anomalies are detected through a behavioral recognition approach. After enabling in IP Zone the profile anomaly detection for a subnet or host, RRDTool builds a behavioral traffic graph for a 24-hour period which can be viewed in Reports » IP Addresses » [Subnet] » Profile Graphs. Wanguard Sensor detects any activity that deviates from the expected traffic levels of the protected subnets, albeit only for the IP decoder.
In practice, the Threshold Anomalies approach is much more reliable and useful. Profile anomaly detection is possible only for hosts and subnets that have a predictable traffic pattern, so larger subnets have a much more predictable traffic pattern than smaller subnets. To reduce the number of false positives, adjust the deviation percent and minimum packet and bit rates, or use the more reliable method of defining thresholds.
Deviation % represents the maximum allowed deviation from the expected traffic before triggering a profile anomaly. A value of 100 allows traffic up to twice (100% expected + 100% deviation) the expected value.
Users should not modify the values from the Advanced Profiling Parameters panel.