29. General Settings » User Authentication¶
If you need to configure LDAP or RADIUS authentication, or if you want to show pop-up notifications during/after login, go to Configuration » General Settings » User Authentication.
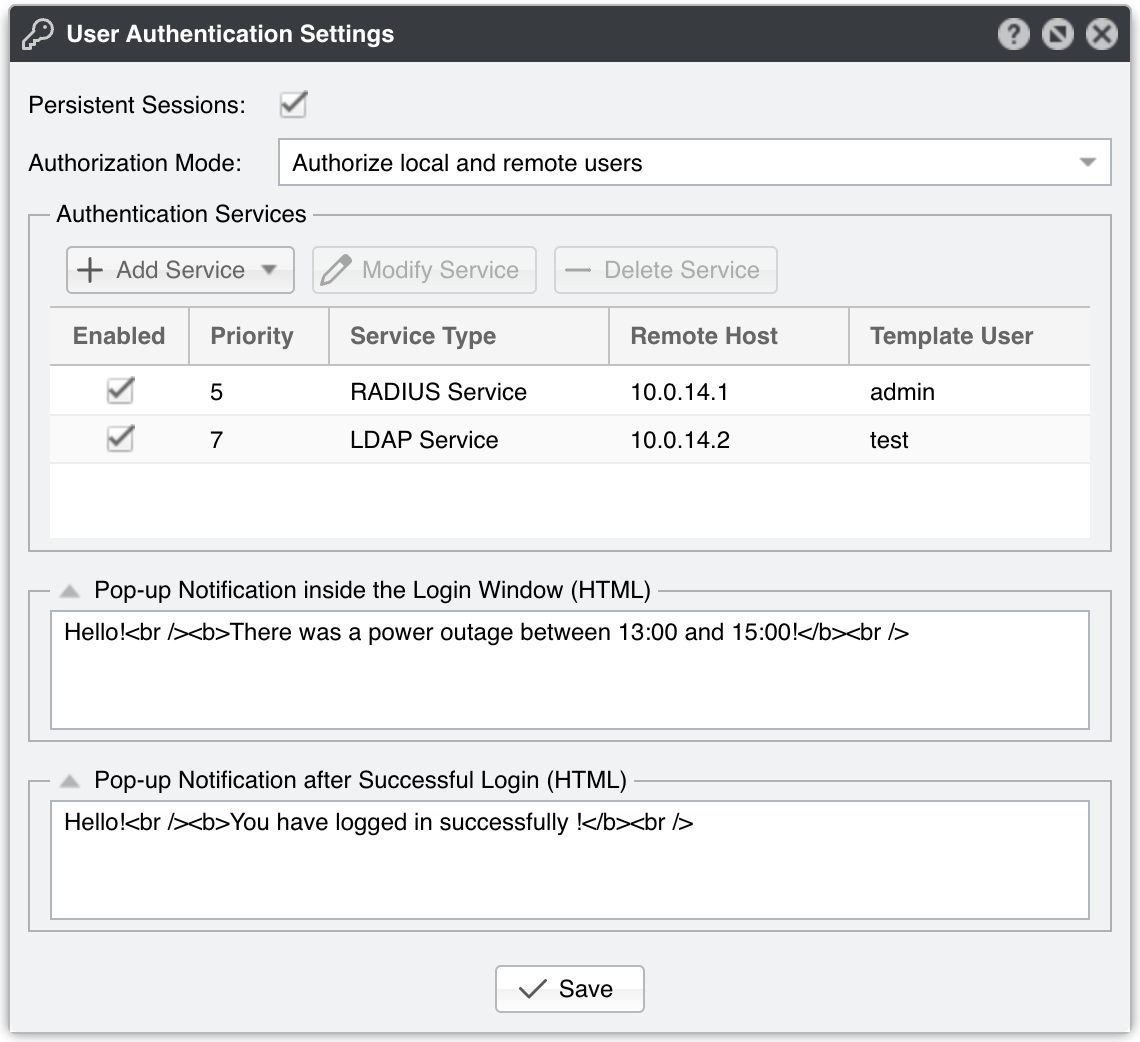
User Authentication Settings parameters:
● Persistent Sessions – When checked, it enables cookie-based authentication for the users that select the Remember checkbox from the login page. Once authenticated, for the next 30 days all subsequent sessions will skip the login page
● Authorization Mode – Select when the Authentication Services listed below can be authorized:
▪ Authorize only local users – The Authentication Services will be used to authenticate only the users defined in General Settings » User Management which have the Authentication parameter set to Remote Authentication
▪ Authorize local and remote users – Also permits the authentication of users not defined in General Settings » User Management but which can be authenticated by the Authentification Services listed below
● Authentication Services – In this grid you can add the LDAP or RADIUS servers used for authentication
● Pop-up Notifications – If you need to show pop-up windows inside the login page or immediately after a successful login, fill in the appropriate fields. The content can be plain text or formatted as HTML
29.1. LDAP¶
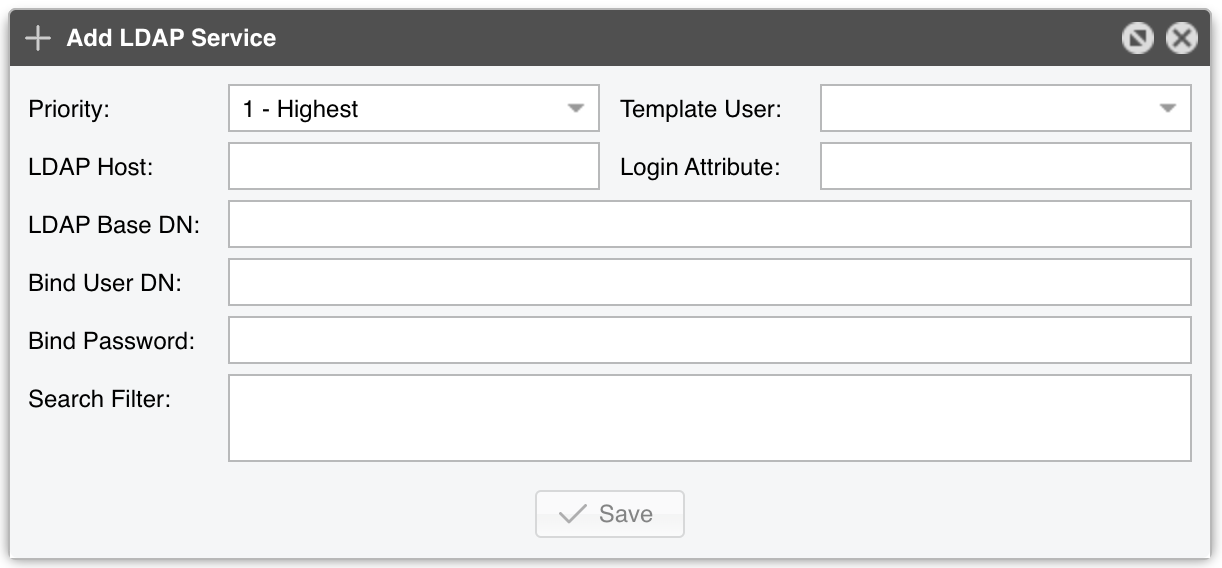
LDAP Service parameters:
● Priority – You can set the order in which Console connects to multiple authentication services. The authentication process stops after the first successful authentication
● Template User – Remotely-authenticated users without a Console account will inherit the privileges of the Template User
● LDAP Host – IP or hostname of the LDAP server. To connect to an LDAP server via SSL, set this parameter as ldaps://<IP>:port/
● Login Attribute – Enter the LDAP attribute that contains the username. For Active Directory it usually is mailNickname or sAMAccountName, for OpenLDAP or IBM Directory Server it could be uid
● LDAP Base DN – Specify the location in the LDAP hierarchy where Console should begin searching for usernames for authorization requests. The base DN may be something equivalent to the organization, group, or domain name (AD) of the external directory: dc=domain,dc=com
● Bind User DN/Password – Distinguished name and password for an LDAP user permitted to search within the defined Base DN
● Search Filter – Can contain rules that restrict which users are authenticated using the current configuration. For example, the string “|(department=*NOC*)(department=ISP)” allows users to authenticate in Console from departments containing the string “NOC” or (|) from the “ISP” department
Note
- For troubleshooting the LDAP Service, you can use two commands:
- ✔ tcpdump -i <ethernet interface> -n -X host <LDAP IP> will show the packets exchanged between the Console and the LDAP Host✔ ldapsearch -x -LLL -H “<LDAP Host>” -x -D “<Bind User DN>” -b “<LDAP Base DN>” -w “<Bind Password>” -E pr=2000000/noprompt -o ldif-wrap=no will dump the whole LDAP structure, which is useful when looking for the right Search Filter
29.2. RADIUS¶
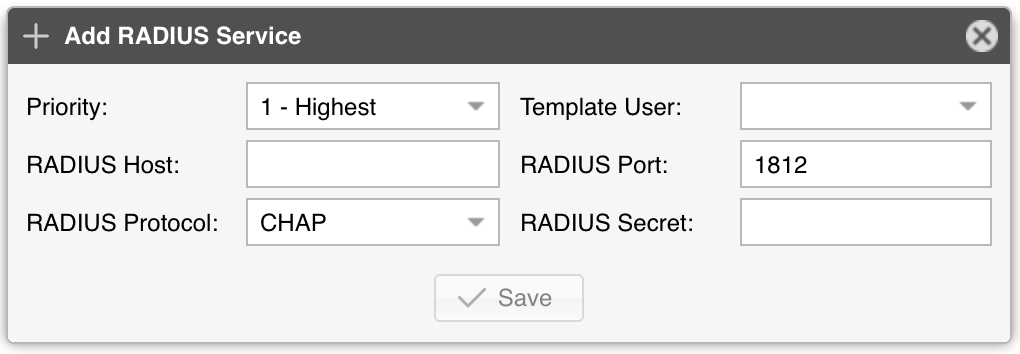
RADIUS Service parameters:
● Priority – You can set the order in which Console connects to multiple authentication services. The authentication process stops after the first successful authentication
● Template User – Remotely authenticated users without a Console account will inherit the privileges of the Template User
● RADIUS Host – IP or hostname of the Radius server
● RADIUS Port – Port through which the Radius server is listening for authentication requests
● RADIUS Protocol – Protocol used for authentication purposes:
▪ PAP (Password Authentication Protocol) – Provides a simple method for the peer to establish its identity using a 2-way handshake
▪ CHAP (Challenge-Handshake Authentication Protocol) – Authenticates a user or network host to an authentication entity
▪ MSCHAP – Is the Microsoft version of the Challenge-handshake authentication protocol, CHAP
▪ MSCHAP2 – Is another version of Microsoft version of the Challenge-handshake authentication protocol, CHAP
● RADIUS Secret – Enter the credentials for connecting to the Radius server