11. General Settings » Anomaly Mitigation¶
In Configuration » General Settings » Anomaly Mitigation, you can configure and fine-tune the behaviour of Wanguard Filter.
Note
The configuration options are relevant only for the selected tab/decoder. The list of decoders can be changed in Configuration » General Settings » Anomaly Detection.
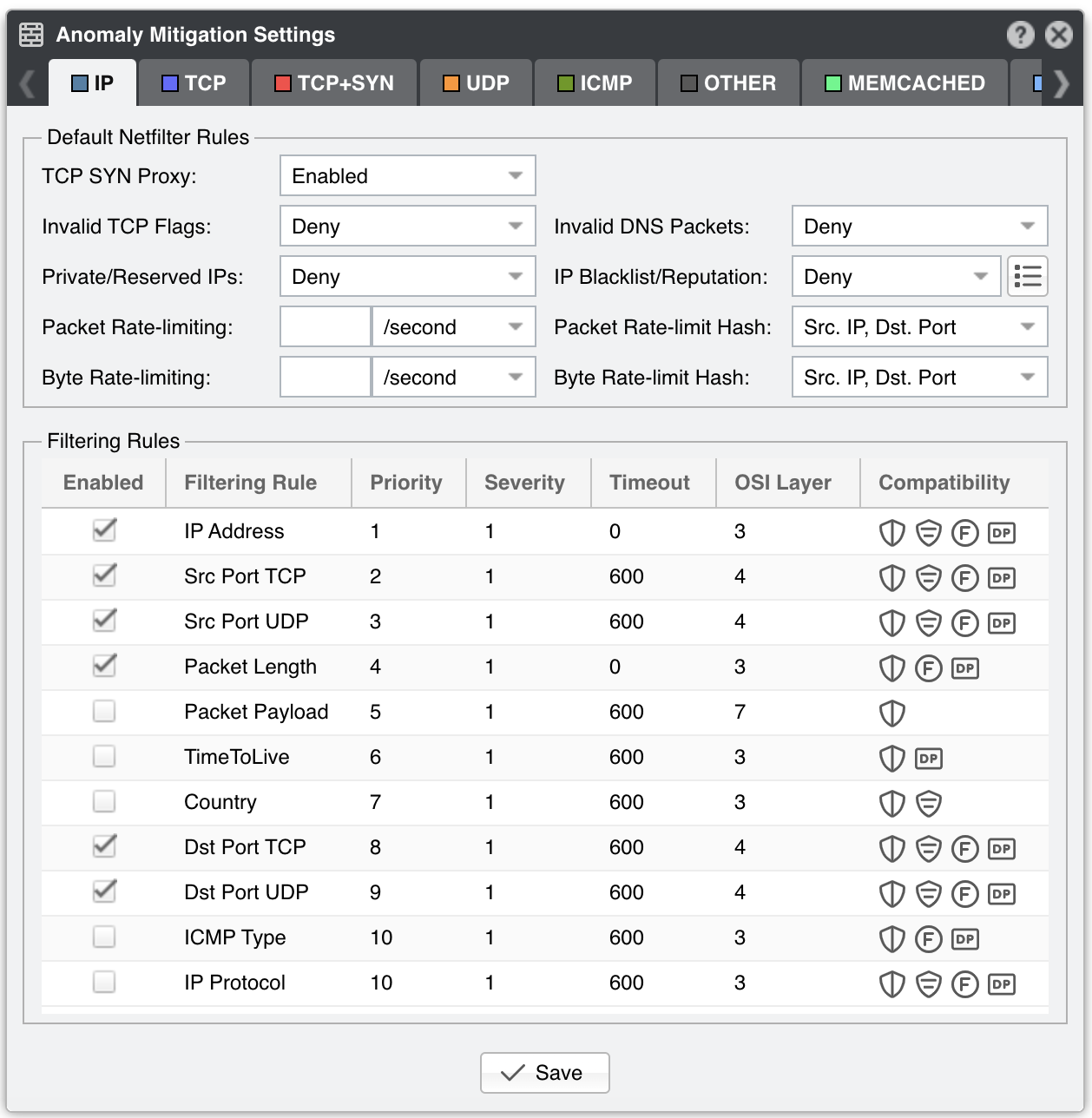
11.1. Default Netfilter Rules¶
The following rules are applied by default when using the Netfilter firewall:
● TCP SYN Proxy – When enabled, Wanguard Filter activates a SYN proxy mechanism provided by Netfilter immediately after its initialization. This mechanism shields servers from SYN flood attacks using a SYN proxy implementation to verify the WAN clients before forwarding their connection requests to the protected server. For this option to work, Wanguard Filter must be deployed inline and must receive both incoming and outgoing traffic.
When the filtering server applies a SYN proxy to a TCP connection, it responds to the initial SYN packet with a manufactured SYN/ACK reply waiting for the ACK in response before forwarding the connection request to the server. Devices attacking with SYN flood packets do not respond to the SYN/ACK reply. The firewall identifies them by their lack of this type of response and blocks their spoofed connection attempts. SYN proxy forces the firewall to manufacture a SYN/ACK response without knowing how the server will respond to the TCP options normally provided on SYN/ACK packets.
Some of the commands necessary to enable the SYN Proxy feature are listed below. This guide does not cover all the necessary configuration steps for enabling SYN proxy.
[root@localhost ~]# echo 1000000 > /sys/module/nf_conntrack/parameters/hashsize
[root@localhost ~]# /sbin/sysctl -w net/netfilter/nf_conntrack_max=2000000
[root@localhost ~]# /sbin/sysctl -w net/netfilter/nf_conntrack_tcp_loose=0
[root@localhost ~]# /sbin/sysctl -w net/ipv4/tcp_timestamps=1
● Invalid TCP Flags – Wanguard Filter can block all invalid TCP flags immediately after its activation. The necessary filtering rules for this option are applied by the Netfilter firewall for traffic forwarded to/from the attacked destination
● Invalid DNS Packets – Wanguard Filter can block all invalid DNS traffic (illegal combination of source port and destination port) immediately after its activation. The necessary filtering rules for this option are applied by the Netfilter firewall for traffic forwarded to/from the attacked destination
● Private/Reserved IPs – Wanguard Filter can block immediately after its activation all private or reserved IPv4 or IPv6 subnets. The necessary filtering rules for this option are applied by the Netfilter firewall for traffic forwarded to/from the attacked destination
● IP Blacklist/Reputation – Wanguard Filter can block all blacklisted IPs immediately after its activation. The necessary filtering rules for this option are applied by the Netfilter firewall for traffic forwarded to/from the attacked destination.
The [IP Blacklist Options] button allows you to select the lists of IPs with bad reputation. This option should be utilized only for a relatively small number of blacklisted IPs, as it may affect the firewall performance and the routing/forwarding process. The maximum number of blacklisted IPs is 65535
● Packet Rate-limiting – You can use this parameter to limit the rate of packets per time unit to a predefined value or to a percentage of the anomaly threshold when the value entered ends with the character “%”
● Packet Rate-limit Hash – You can apply the packet rate-limiting globally to a single object (Src. IP, Src. Port, Dst. IP, or Dst. Port) or any combination of objects. If the rate-limiting should be connection-oriented, select all objects. To rate-limit the packet rate of each source IP, select the Src. IP object
● Byte Rate-limiting – You can use this parameter to limit the rate of bytes per time unit to a predefined value or to a percentage of the anomaly threshold when the value ends with the character “%”
● Byte Rate-limit Hash – You can apply the byte rate-limiting globally to a single object (Src. IP, Src. Port, Dst. IP, or Dst. Port) or any combination of objects. If the rate-limiting should be connection-oriented, select all objects. To rate-limit the byte rate of each source IP, select the Src. IP object
11.2. Filtering Rules¶
The Filtering Rules grid shows the filtering rule types available for the selected decoder, and permits the editing of filtering rule parameters.